|
Aslan REVISITED !!! |
|||||||||||||||||||||
| :: Introduction (words from the author) | |||||||||||||||||||||
|
UPDATE: I have decided it is good to know about some references here, first of all the topic of binary translation/code rewriting techniques (either static or dynamic)/binary code manipulation tools were used in the past - like in for example QPT(1994), Shade(1994), ATOM(1994), NJMC(1994), EEL(1995), Freeport Express(1995), FX!32 (1996) etc. The PE integration itself was also used by Zombie in Mistfall engine (somewhere in 2000). However the "welding" feature was not introduced back then. Besides Aslan does not rely on other integration engine code.
|
|||||||||||||||||||||
| :: BINARY CODE WELDING | |||||||||||||||||||||
|
|
|||||||||||||||||||||
| :: EXAMPLE (WELDING TWO HLL APPS INTO ONE) | |||||||||||||||||||||
|
So what we should take from LESSON4.EXE? In order to make the correct welding happen we need to split bytes from LESSON4.EXE for code and data (often needs to be writable so we need to locate it in the proper segment). Following table shows what fragments do we need:
As you probable know Aslan provides you unique abilities and allows you to inject code into any particular location in the original PE file (of course it should be logical). For the sake of this example i have chosen following injection points:
Injection points original disassembly:
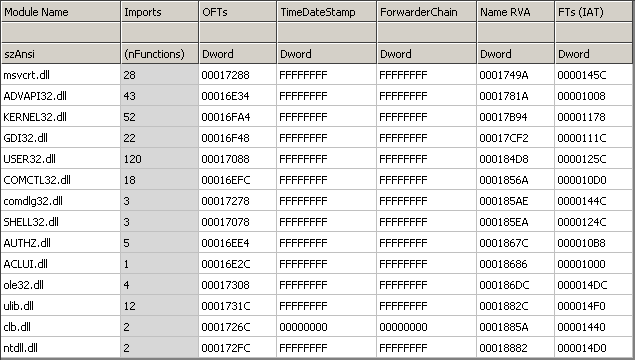
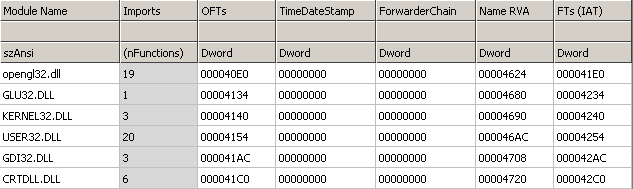
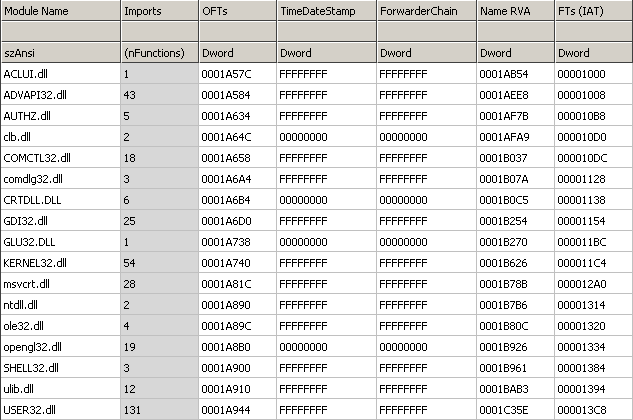
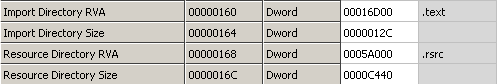
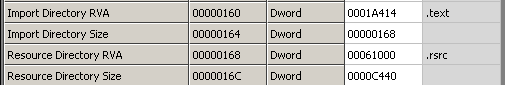
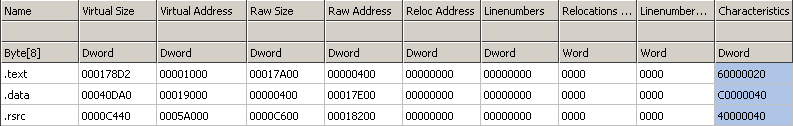
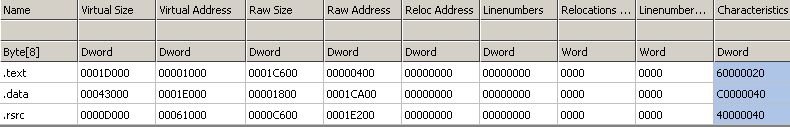
It means that every instruction (every area marked as code -> 0x00401000-0x00401FC4) from LESSON4.EXE will be injected at 0x010062C7 (.text section) of original REGEDIT.EXE application. Analogous the DATA from LESSON4.exe (0x00402000-0x004025FF and 0x00403000-0x00403340) will be put at 0x01019020 (.data section r&w) in original REGEDIT.exe application. WHAT ABOUT IMPORTS? As you probably know REGEDIT.EXE is using some different imported APIs and libraries than LESSON4.EXE. This is shown on the following pictures: As you can see some libraries are missing like opengl32.dll/glu32.dll etc. You can belive me or not but even when same library is used in two files specified imported APIs are still missing. Aslan is able to disassemble both of the import tables to some intermediate representation, join them together (if of course this is needed, so if a wanted API is already imported by REGEDIT.EXE there is no need to declare it one more time). The newly created import table can be also stored at any position in the PE file as long as it stays valid. Some of the know PE utilities like CFF Explorer have some features like ImportAdder but they always put additional imported entries at the end of the file - Aslan does not work that way! When all the imports are resolved Aslan links them with requests from LESSON4.EXE code. Now all the LESSON4.EXE code looks like it came just out from the linker. Here is the final import table: As you can see now the final import section is quite bigger. Following pictures will show you that even if the imports are now bigger the import directory still resides in the same PE section (first section - .text). Additionally the number of sections between the original program (REGEDIT.exe) and the welded one is the same, and also the resources directory points to the same section (.rsrc):
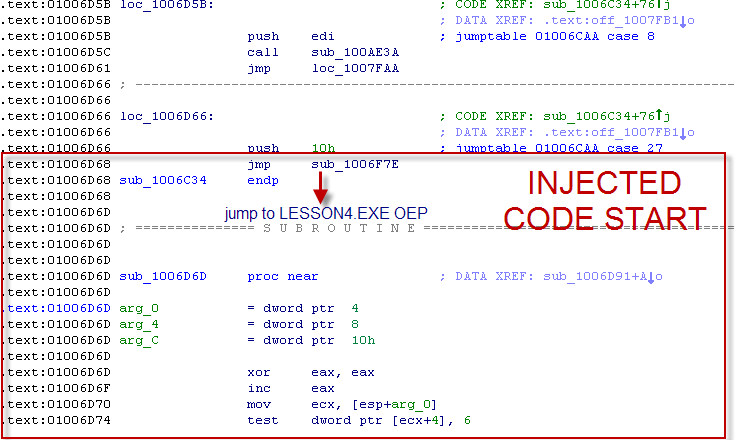
Where at 0x01006D68 an unconditional jump is placed, which throws the execution to the orignal LESSON4.EXE entrypoint just like the following picture shows: And this is "all done" by following piece of code:
|
|||||||||||||||||||||
| :: Sample binaries (original REGEDIT.EXE, LESSON4.EXE and REGEDIT_WELD.EXE) | |||||||||||||||||||||
|
|
|||||||||||||||||||||
| :: Video demo (running REGEDIT_WELD.EXE) | |||||||||||||||||||||
|
You can check the video in HD using this link: http://vimeo.com/5550537 (password: 'die')
Aslan from Piotr Bania on Vimeo.
|
|||||||||||||||||||||
| :: Last words | |||||||||||||||||||||
|
Summing it up: Aslan engine can rebuild all the PE structure, internal offsets (jumps, references etc.), any type of PE directories like relocs, imports, exports, resources...) - all is done automatically. Additionaly now it can also meld programs written in High Level Lanaguages like C!!! Of course i haven't described Aslan mechanisms deeply, this is obvious since i don't want to write a book about it :-) This project is still in development phase,
however even if I finish it
i doubt i will release it for public. This is obvious since most of
people would use it for evil purposes and in the end it will not
bring me much good karma. Besides i have decided to delete entire GUI so
right now Aslan has no interface so i am probably the only person
who can use it correctly (not to mention Marcin Miœta's cat :-)). I
did it for fun additionally it helps me with "pentests".
|
|||||||||||||||||||||
www.piotrbania.com
2009 - All rights reserved ®
Copyrights © - Piotr Bania